Selected Works
-

Understanding Memory Management, Part 1: C
The first in a series on how memory management works, starting with C and ending in Rust with a planned detour through garbage collection.
-

An overview of browser privacy features
How browser features like private browsing mode, TCP, and anti-fingerprinting protect you from tracking, and when they don't.
-
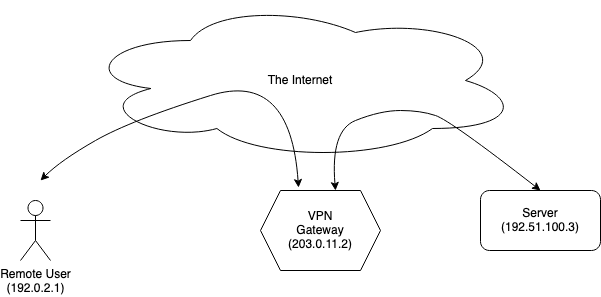
How to hide your IP address
A field guide to VPNs, proxies, and traffic relaying
-

Everything you never knew about NATs and wish you hadn't asked
The first in a four-part series on a ubiquitous and yet reviled network technology
Complete Archive
- Using Government IDs for Age Assurance
- Ultra Tour Monte Rosa (UTMR) Race Report
- Olympic Grand Loop (Deer Park Loop)
- Understanding Memory Management, Part 7: Advanced Garbage Collection
- Understanding Memory Management, Part 6: Basic Garbage Collection
- Understanding Memory Management, Part 5: Fighting with Rust
- Understanding Memory Management, Part 4: Rust Ownership and Borrowing
- Understanding Memory Management, Part 3: C++ Smart Pointers
- Understanding Memory Management, Part 2: C++ and RAII
- Understanding Memory Management, Part 1: C
- Why it's hard to trust software, but you mostly have to anyway
- Overloaded fields, type safety, and you
- River of No Return 108K Race Report (2024)
- New EV Habits for ICE Vehicle Owners
- Notes on Post-Quantum Cryptography for TLS 1.2
- How to manage a quantum computing emergency
- Design choices for post-quantum TLS
- Sean O'Brien 100K Race Report (2024)
- A hard look at Certificate Transparency: CT in Reality
- A hard look at Certificate Transparency, Part I: Transparency Systems
- Adventure Run Report: Northern Yosemite 50
- Maybe someday we'll actually be able to search the Web privately
- Desolation Wilderness Seven^H^H^H^H^HTwo Summits
- Private Access Tokens, also not great
- The endpoint of Web Environment Integrity is a closed Web
- How NATs Work, Part IV: TURN Relaying
- Broken Arrow Triple Crown Race Report
- How NATs Work, Part III: ICE
- Defending against Bluetooth tracker abuse: it’s complicated
- How NATs Work, Part II: NAT types and STUN
- Everything you never knew about NATs and wish you hadn't asked
- Architectural options for messaging interoperability
- Network-based Web blocking techniques (and evading them)
- Internet Transport Protocols, Part I: Reliable Transports
- Surprise, blockchains won't fix Internet voting
- How to securely vote for (or against) Elon Musk
- One does not simply destroy a nuclear weapon
- Can we agree on the facts about QWACs?
- First impressions of Bluesky's AT Protocol
- How to hide your IP address
- Self-Driving Vehicles, Monoculture, and You
- On the Security and Privacy Properties of Public WiFi
- ELI15: PCR and PCR Testing
- Ultra-Trail du Mont-Blanc (UTMB) Race Report
- ELI15: Private Information Retrieval
- Can we make Safe Browsing safer?
- Discovery Mechanisms for Messaging and Calling Interoperability
- Pacifica Foothills Race Report
- Verifiably selecting taxpayers for random audit
- Tenaya Loop Adventure Run 2: Redemption
- An overview of browser privacy features
- Understanding The Web Security Model, Part VI: Browser Architecture
- First impressions of Web5
- On Blockchains/Ledgers and Identity Systems
- Understanding Online Identity
- Notes on Multiple Encryption and Content Filtering
- End-to-End Encryption and the EU's new proposed CSAM Regulation
- Understanding The Web Security Model, Part V: Side Channels
- Challenges in Building a Decentralized Web
- Understanding The Web Security Model, Part IV: Cross-Origin Resource Sharing (CORS)
- Lake Sonoma 50 Race Report
- End-to-End Encryption and Messaging Interoperability
- What's with the www prefix in www.example.com?
- Understanding The Web Security Model, Part III: Basic Principles and the Origin Concept
- Understanding The Web Security Model (Outtake): Cookies and Behavioral Advertising
- Understanding The Web Security Model, Part II: Web Applications
- Understanding The Web Security Model, Part I: Web Publishing
- Games, constraints, and the humanly possible
- Risks (or non-risks) of scanning QR codes
- Overview of Interoperable Private Attribution
- Ensuring Privacy For Age Verification
- DNS Security, Part VII: Blockchain-based Name Systems and Transparency
- DNS Security, Part VI: Blockchain-based Name Systems
- Privately Measuring Vaccine Doses
- DNS Security, Part V: Transport security for Recursive to Authoritative DNS
- Qualifying for prestige races (and why you won't get into Western States)
- DNS Security, Part IV: Transport security for DNS (DoT, DoH, DoQ)
- Privacy for Genetic Genealogy: Happy Goldfish Bowl Everyone
- DNS Security, Part III: DANE and the WebPKI
- DNS Security, Part II: DNSSEC
- DNS Security, Part I: Basic DNS
- A look at the Dutch vaccine passport system
- Privacy Preserving Vaccine Credentials
- Highline Trail Adventure Run Report
- Privacy for license plates
- A quick look at the New Zealand Vaccine Pass
- Privacy Preserving Measurement 5: Randomization
- Modelling grade's impact on running pace
- The EU vaccine passport compromise and how to (maybe) fix it
- Sean O'Brien 100K Race Report
- Privacy Preserving Measurement 4: Heavy Hitters
- Privacy Preserving Measurement 3: Prio
- Privacy Preserving Measurement 2: Anonymized Data Collection
- Privacy Preserving Measurement 1: Background
- Fantastic memory issues and how to fix them
- Tenaya Loop Adventure Run Report
- What's an ultramarathon?
- Do you know what your computer is running?
- Perceptual versus cryptographic hashes for CSAM scanning
- SF/Fantasy you should be reading
- What does the NeuralHash collision mean? Not much
- More on Apple's Client-side CSAM Scanning
- Overview of Apple's Client-side CSAM Scanning
- Securing Cryptographic Protocols Against Quantum Computers
- What's wrong with QR code menus?
- A look at the EU vaccine passport
- Bigfoot 73 Race Report
- What the heck is going on in New York's election?
- Science's broken publishing model
- What's in California's Vaccine Passport?
- So you want to watch people run
- Notes on supershoes
- Some Confusion in New York's Vaccine Passport Rollout
- The tech behind EG
- Blockchains/Ledgers and Vaccine Passports
- Against streaming apps
- Improving vaccine registration
- Lights for Running
- The (depressing) future of stalking tech
- Thoughts on personal tracker privacy
- Authentication for Vaccine Passports
- Notes on Implementing Vaccine Passports
- Some stuff about running pacers
- Addressing Supply Chain Vulnerabilities
- What WebRTC means for you
- Why getting voting right is hard, Part V: DREs (spoiler: they're bad)
- Why getting voting right is hard, Part IV: Absentee Voting and Vote By Mail
- Why getting voting right is hard, Part III: Optical Scan
- Why getting voting right is hard, Part II: Hand-Counted Paper Ballots
- Why getting voting right is hard, Part I: Introduction and Requirements
- A look at password security, Part V: File and Disk Encryption
- Subject: A look at password security, Part IV: WebAuthn
- A look at password security, Part III: More secure login mechanisms
- A look at password security, Part II: Web sites
- A look at password security, Part I: history and background
- COVID Surveillance Part 2: Mobile Phone Location
- Looking at designs for COVID Contact Tracing Apps